24. Securing Linux at the OS Level
Securing Linux at the OS Level
ND545 C02 L02 A20 Securing Linux At The OS Level
Securing Linux at the OS Level Notes
Recap:
- Linux often enters organizations due to applications that run on it.
- It is not uncommon for those servers to be neglected from patching and proper permissions. This increases an organization's attack surface.
- Encrypting the server disks is recommended for all servers.
- Disable root SSH access.
- No 777 permissions!
- Just like with Windows Services, evaluate if there are any Daemons that can be disabled.
- Linux Permissions work similar to windows, practice the Principle of Least Privilege after performing an audit of existing permissions.
Key Terms
- Daemons: are a small computer program that runs as a background process, rather than being under the direct control of an interactive user.
- 777 Permissions: Is a level of Linux permissions that means making the file readable, writable, and executable by everyone.

Linux Best Practices
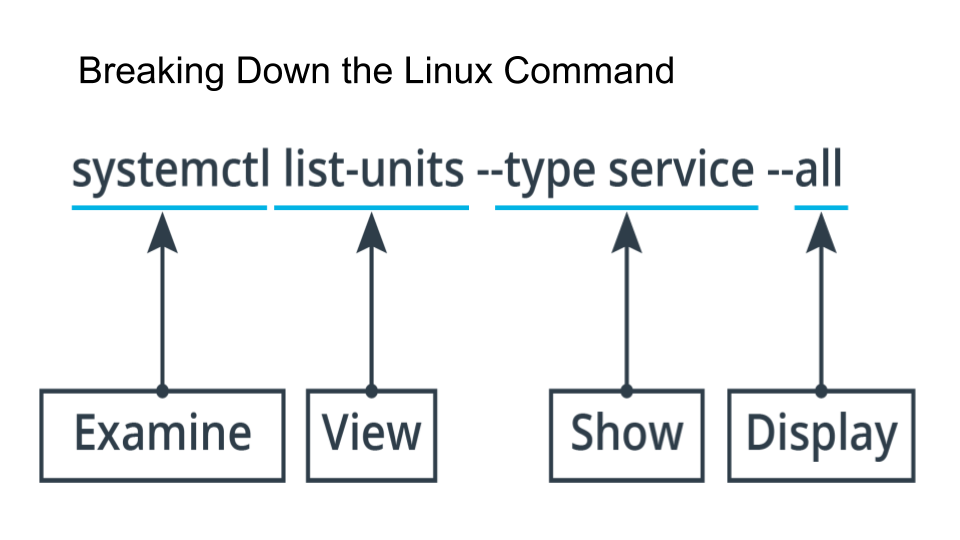
Command
systemctl list-units --type service --all
Use the command above to evaluate the services or daemons that are running on CentOS.
ND545 C02 L02 A21 Securing Linux At The OS Level Walkthrough